Last Updated on April 28, 2023
As the Internet of Things (IoT) continues to grow, transforming the way we live and work, it should be expected that there will be various security challenges to battle. This means that as a business owner, you should be ready to secure your devices and connections.
Statista reports that there are currently 15.14 billion IoT-connected devices worldwide. While some manufacturers work hard to constantly improve how the Internet of things works, it is important that you know what you are up against in terms of security. Keep reading to learn about five common IoT security issues and how to protect your devices, networks, and data from them.
Lack of security in devices
Most IoT devices are manufactured with little or no security, according to research by the Aberdeen group. The absence of proper security in these devices makes them more prone to cyber-attacks. As a result, companies have experienced network breaches that led to the theft of sensitive information, unauthorized remote access to devices, and control by attackers.
Back in 2021, news of the Verkada security breach came to light. Verkada is a provider of cloud-based video surveillance and security solutions, which use IoT devices to monitor various facilities and environments. A group of hackers had gained access to Verkada’s systems, compromising their customer credentials and devices.
This breach clearly indicates the importance of security in IoT devices and the need for organizations to be proactive in protecting access to their systems. Here are some steps you can take to ensure that your devices are not compromised:
- Conduct manufacturer research before purchasing devices. You want to get devices from manufacturers and service providers that have a good track record.
- Use devices that have strong encryption, secure communication protocols, and the ability to receive software updates and patches.
- Use strong and unique passwords on your devices instead of generic passwords that are easy to guess.
- Use secure network connections such as a virtual private network (VPN) or a separate, dedicated IoT network. This will reduce the risk of hacking and other security breaches.

You should also consider using a security solution, such as antivirus software, or a security information and event management (SIEM) system, to protect your IoT devices and network from cyber threats.
Finally, always monitor your IoT devices for any unusual activity, such as unauthorized access attempts or data breaches.
Inadequate network security
IoT devices rely on networks to communicate and exchange data. However, these networks are often inadequately secured, making them vulnerable to IoT security issues like hacking, man-in-the-middle attacks, and other security concerns.
For instance, devices that are connected to public wireless networks are more susceptible to hacking and other security breaches. Attackers can easily send malware to their devices through these public connections which are more likely to be unsecured.
Also, hackers can easily monitor device networks and steal sensitive business and customer data while going unnoticed. Due to poor network security, imposters can send fake notifications like the example below. These notifications come with harmful links which unsuspecting device users may click on, granting the bad actors access to their systems.
With man-in-the-middle attacks, a hacker intercepts the communication between two devices that are connected over a network. This will allow the hacker to access the data in transmission or gain control over the devices.
To stay protected, you should regularly update your network security and avoid connecting your devices to public networks. In your organization, you should ensure that only authorized devices (preferably company-owned devices) can be connected to your network.
Ensure that you use secure protocols, such as HTTPS SSL/TLS Certificates with best practices in mind, to protect the data transmitted between your devices and the network. Do not forget about end-to-end encryptions too. Additionally, use firewalls to prevent unauthorized access to your network and protect your devices from cyber-attacks.
Also, educate your employees not to respond to suspicious emails or notifications on their devices as they could unknowingly grant access to hackers by doing so. Finally, disable any unneeded network services to reduce the risk of getting attacked.
Weak authentication
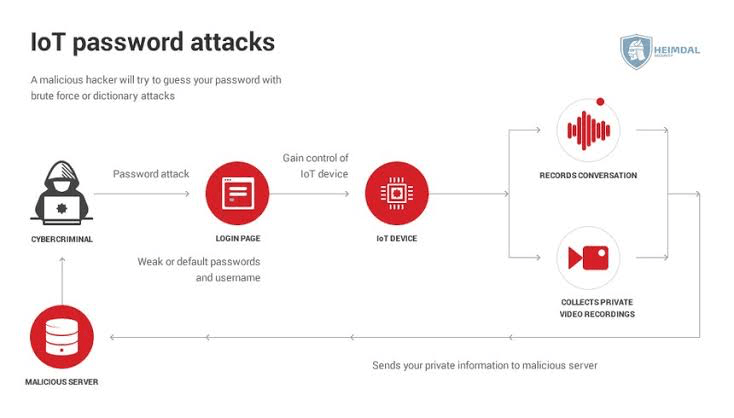
IoT devices often have weak authentication methods, making it easy for attackers to impersonate legitimate users and gain access to sensitive data. In addition, many devices use the same default passwords, which can be easily cracked by hackers.
IoT devices often possess applications like payment apps, communication platforms, and database management software. These applications hold sensitive data and should be thoroughly protected with strong security measures like user authentication before access.
Devices with weak password authentication methods are prone to data breaches. Hence, you will be at risk of losing your personal data or sensitive business information.
Further, IoT device manufacturers and software providers often use default passwords and login credentials. Failure to change this and integrate proper authentication structures potentially leads to brutal attacks on your device. For instance, the Mirai malware variant, Miori, actively scans IoT devices for weak passwords, making it easier for hackers to do their dirty jobs.
With this in mind, you should actively protect your devices and connections by using strong passwords to secure access to your applications. Also, enable two-factor or multi-factor authentication on your IoT devices and network.
Some applications allow you to receive One-Time Passwords (OTPs) on your mobile devices or through your email. Do not hesitate to maximize these options. This way, you will be alert to potential threats and unauthorized attempts to access your IoT devices and platforms.
Lack of software updates and patches
Because hackers are actively trying to outdo security protocols on IoT products, software updates are necessary. When IoT devices are not updated, they will be vulnerable to emerging security threats and malware attacks. So, if manufacturers fail to release patches and updates for devices, they give potential attacks and other IoT security issues free room to roam and exploit known vulnerabilities.
However, IoT devices may be difficult to update for several reasons. First, the device could be designed with limited processing power, making it difficult to install and run software updates. Also, manufacturers are constantly introducing new products. So, in a bid to encourage the adoption of these new products, they may completely neglect to create software updates for older devices.
In addition, the update process for many IoT devices is often slow and inefficient, making it difficult to keep devices up-to-date with the latest security patches and software updates. IoT devices also come from a wide variety of manufacturers, with different operating systems, software versions, and hardware configurations. This makes it difficult to develop and distribute security patches that are compatible with all devices.
You should be intentional about updating your IoT devices and software. Manufacturers will do well to notify you when these updates are available. However, beware of fake security updates and pop-ups. In cases where older devices have been compromised, do well to ensure that you transition to more recent products for the safety of your device and useful resources.
Limited regulatory oversight
There are currently limited regulations in place to ensure the security of IoT devices. One reason for this is that the Internet of Things is a rapidly evolving field, with new devices and technologies being developed and introduced to the market. This can make it difficult for regulators to keep up and enforce regulations in a timely manner.
Also, the nature of IoT devices—which often connect across national borders and operate in a decentralized manner—can make it difficult to determine which regulatory bodies have jurisdiction over them.
According to IEEE, governments and regulators may be hesitant to implement strict regulations for IoT devices out of concern that this may stifle innovation—and impede the growth of the IoT market.
In many cases, regulations for IoT devices are based on voluntary standards set by industry organizations, rather than mandatory government regulations. This can result in a patchwork of standards that vary from region to region and from device to device.
Despite these challenges, there is a growing recognition of the need for stronger regulatory oversight of IoT devices to ensure their security and privacy.
Recently, several countries and organizations have taken steps to establish regulations and standards for IoT devices. However, more work is needed to ensure that these regulations are robust, enforceable, and effective in preventing IoT security issues and the losses they generate.
In Closing
It is no doubt that IoT security issues can cost your organization a lot of money, time, and resources. First and foremost is the lack of security in the devices themselves that makes them vulnerable to cyber-attacks and data breaches.
Inadequate network security is also a major concern, as IoT devices are often connected to the internet, making them a prime target for hackers. Weak authentication protocols can also leave your devices vulnerable.
The lack of software updates and patches for IoT devices is another major challenge, as it leaves the door open for hackers to exploit security vulnerabilities in the device software. Additionally, the limited regulatory oversight on device requirements means that manufacturers who do not have in-house regulations can simply neglect necessary security measures in their products.
Despite these challenges, there are steps you can take to improve the security of your IoT devices. You can ensure better network security by implementing strong passwords and using encryption, and you can also stay on top of software updates and patches to keep your devices up-to-date with the latest security measures.
By staying informed about these security challenges and taking steps to mitigate the risks, you can safely ensure the security of your IoT devices. ~ by Paul Baka