Last Updated on January 3, 2023

Bring Your Own Device (BYOD) is quickly becoming the new standard in hybrid workplace technology. BYOD programs allow employees to use their personal devices for work and get appropriately reimbursed.
This is a great cost control option, providing more efficiency because of flexibility and convenience – particularly for companies looking for scalability.
However, it can also prove to be a risky choice because while company phones protect sensitive work communications, organizations that rely on the personal phones of employees unintentionally create high risks in business operations around security, safety, and insurance. Fortunately, there are some steps you can take to make hybrid working as efficient as possible for your organization. Read the rest of this article to discover some of the biggest security threats to BYOD workplace environments, and the steps you can take to mitigate those risks.
BYOD Challenge #1: Unclear Security Protocols
Unclear protocols are among the most significant BYOD security risks faced by organizations today.
For example, some employees use their smartphones to connect to their emails so they can get ahead and ease their workload. Other workers use their own Google or Apple ID which allows these personal logins to synchronize data to the cloud for all devices associated with the account.
Both of these examples often result in unforeseen vulnerabilities where businesses unwittingly expose themselves to data theft.
With just these two examples, it is clear to see that while BYOD can be a huge boost to productivity, it can also lead to massive security threats when a company’s intellectual property follows workers out of the building at the end of the day.
Solution: BYOP AUP (Acceptable Use Policy)
To prevent the damage that can be wrought by seemingly small mistakes like the ones outlined above, your organization needs to implement an acceptable use policy (AUP) that clearly defines, communicates, and enforces strong security policies for all users that access company data using the BYOD program.
For example, you might define the applications that are allowed and those that are not, as well as any websites that employees can access while on the company network.
According to recent reports, the majority of workers access online services like video conferencing systems, personal messengers, and collaboration tools without even notifying IT, as shown by the graph below:
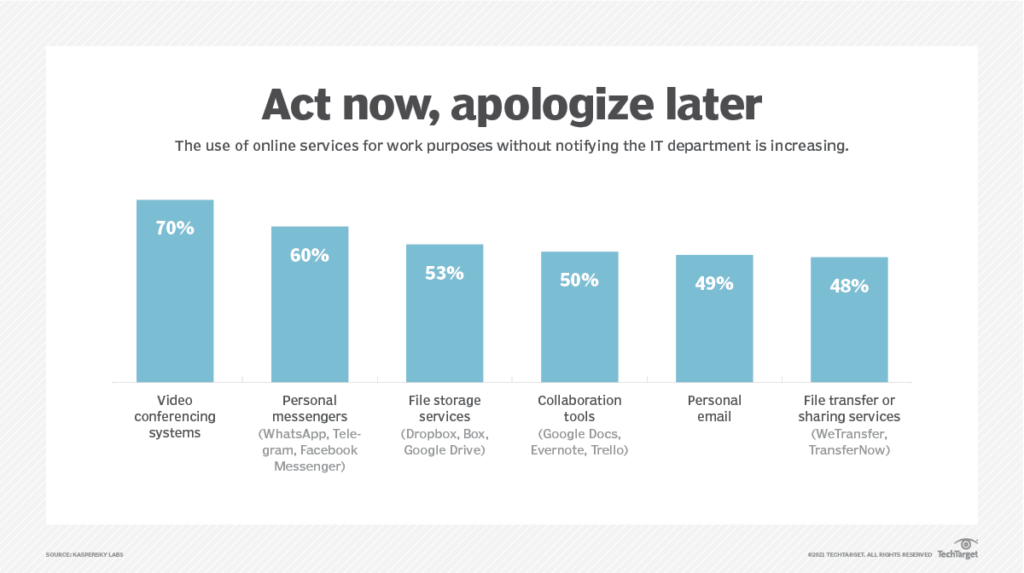
This is one of the reasons why companies need a clearly defined policy for acceptable use of such apps and websites. Make sure this is communicated to everyone in your employee base who will be using their own devices to access the work network.
Neal Taparia, who runs the gaming platform Solitaired, explains you should also educate users on why you have an AUP. “We explain to our employees why we have these policies so they can be more aware of device usage vulnerability. We also make clear that we don’t want anything to happen that can compromise our gamers.”
BYOD Challenge #2: Compromised Data
One of the main reasons why BYOD is such an attractive trend for modern organizations is that it allows employees to leverage their own preferred endpoints for work-related activities so they can use the resources they prefer.
However, this is also the same reason why BYOD is perhaps the biggest security threat companies face today. There are blurred lines between company resources and personal resources which often leads to huge issues and network security.
Solution: BYOD MDM (Mobile Device Management)
As with most of the BYOD risks we will look at in this article, the issue of compromised data can be mitigated by using a mobile device management solution. You need a secure workspace that isolates and protects work from personal use, and a reliable MDM allows for centralized management of all mobile devices that use your company network.
Some MDM software tools come out of the box with SSO, 2FA, identity management, and device security checks.
With the software in place, you now have the ability to perform security patching, application management, updates, etc. on all mobile devices that are enrolled with your program. This will allow you to boost security and privacy while decreasing the number of potentially vulnerable devices within your network.
Note: You might also consider Enterprise Mobility Management (EMM). This is similar to MDM, except that EMM manages the entire device whereas MDM manages all the device’s features.
BYOD Challenge #3: Unsecured Wi-Fi Access
This is yet another security issue that can arise if your company allows workers to use their own devices for work-related activities.
Employees sometimes use free Wi-Fi and hotspots to access your company network which can leave the door open for unscrupulous people to snoop or hijack sessions to steal your company information.
Solution: BYOD Awareness Training
One way to mitigate this risk is to provide awareness training for all BYOD end-users. User awareness training is an important part of maintaining security in any organization, but it is especially important for companies that use BYOD policies.
End-user awareness training can include educating employees on the following:
- Enforcing strong passwords on personal devices
- Safe internet habits
- Data security management
… and more.
Depending on your organization’s culture, you can roll out this training as often as once a month or on a less frequent basis. At the bare minimum, you should train end users at least once a year to ensure that everyone is kept up-to-date with the latest security best practices. This can be done with relative ease using a popular online course platform.
BYOD Challenge #4: Device Theft or Loss
Many organizations have had to deal with catastrophic consequences resulting from device loss or theft. Mobile devices, in particular, are the easiest endpoints to lose, which makes them especially risky in BYOD workplace security.
These risks are magnified further if workers do not follow the company’s security procedures. For example, if they have a weak password for any of their applications, it makes it that much easier for hackers to get control of the BYOD smartphone.
The worst part is that even with strong passwords, biometric readers, etc., company information can still be accessed by persistent criminals with increasingly sophisticated hacking tools.
Solution: BYOD DLP (Data Loss Prevention) Strategy
Data loss prevention is a strategy for ensuring that end users do not send sensitive or confidential information outside the company network.
A DLP tool applies a policy for each piece of information as it is created. This includes files, emails, or applications. For example, the DLP software might identify content containing personally identifiable information (PII) such as credit card information or an employee’s Social Security number.
In addition to having a strong DLP strategy in place, IT must have measures that can be taken to remotely wipe any stolen devices. Ideally, any user whose device is lost or stolen should alert IT as soon as possible. This will allow them to lock down the compromised unit or wipe it right away.
BYOD devices can be more difficult to secure in such situations. In fact, according to a report from Social Barrel, the ability to remotely wipe BYOD devices is unreasonably low which is why businesses need to set and enforce policies for employees to register all BYOD devices.
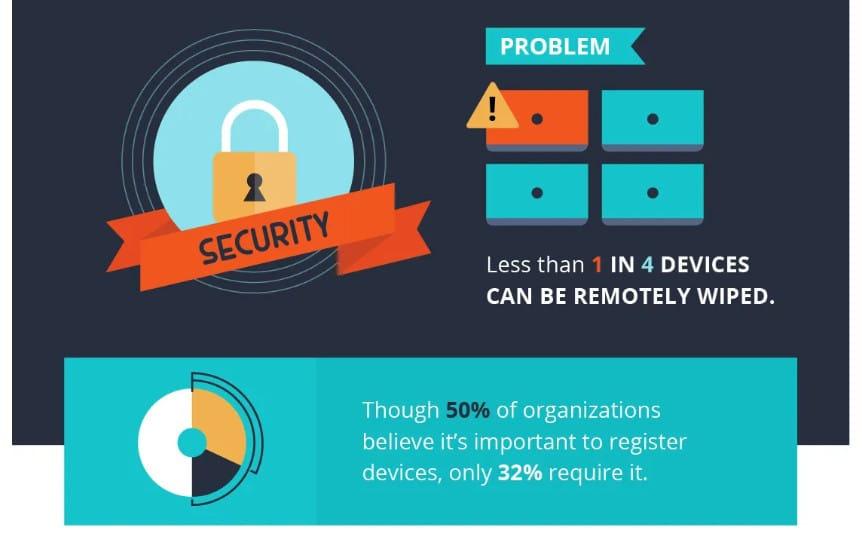
It is a lot easier to wipe devices remotely if reliable mobile device management software was previously installed. The best management platforms will allow IT administrators to determine the following as part of the BYOD security policy:
- How to wipe lost devices
- How long to wait before wiping the device
- Which components of the device should be wiped
…and so on.
BYOD Challenge #5: Mobile Malware
Another huge BYOD challenge is the malware that is storming iPhones and Android phones everywhere.
Every day, unsuspecting smartphone users inadvertently download malware to their devices, allowing malicious actors to pinpoint their location and steal sensitive data.
For the most part, users are unaware that their endpoints have been affected and they will go on to share data with malicious third-party programs without realizing how they are contributing to a huge security risk to their company.
The graph below shows that data leakage from unsafe apps or content is the leading cause for concern in BYOD security:
Solution: Mobile App Management (MAM) Tools
IT departments can use mobile app management tools to secure company data, harden your network, and create policies to keep out jailbroken devices. Jailbreaking refers to the process of removing software restrictions imposed by the manufacturer.
Additionally, IT departments can mitigate this type of data leakage by determining which non-work apps are safe to download onto workers’ devices. Malware is often hidden in innocent-looking programs that you find on the App Store.
End users can also be educated on being more conscious about the permissions they give to various applications. This will help lessen the weak points used by bad actors to pinpoint device locations so they can steal sensitive data.
Choose the Right BYOD Vendor to Mitigate Security Risks
As you have seen, there are many ways your company can benefit from BYOD, but it is crucial to ensure that you have measures in place to deal with any and all privacy and security issues that might crop up in a hybrid workplace.
An effective device management system matters because it is the best way to mitigate risk and prevent a security breach. When you require a security package to run on all BYOD hardware in your program, it reduces the chances of any weak points that can potentially turn into costly security issues.
But, for this strategy to work effectively, you need to choose the right solution to cater to your company’s unique needs.
A great vendor allows you to secure BYOD access for all your employees. But remember, to make hybrid working work, it is important to give employees the freedom to work in ways that allow them to be their most productive while balancing that with your company’s need to pursue an effective business strategy and lessen liability.

Choose a vendor with end-to-end solutions for security, policy, and employee safety in BYOD business environments.
The platform must have a secure workspace for virtual work that isolates all work and protects it from any personal use on the same device. This means your information will remain secure whether the device is BYO or company-owned. The zero-trust software will make it easy for you to decide what users can and cannot do in BYO and managed devices.
This is undoubtedly the easiest way to make hybrid working and BYOD environments work for your business strategy.
Conclusion
Despite all the (significant) security risks bringing your own devices poses to an IT environment, businesses continue to embrace BYOD in hybrid working environments. These types of user-centric programs are alluring because they offer a wide range of benefits relating to everything from increased employee productivity to enhanced employee satisfaction and more.
It is clear that BYOD is here to stay, which is why companies need to find effective ways to address security and privacy issues that arise as a result of this practice.
We hope this guide has helped you gain a better understanding of what it takes to implement and run an efficient bring-your-own-device program. If you are already running a BYOD workplace program or are planning to start in the near future, use the information in this article to help you keep your data secure.
With your BYOD security policies and risk management strategies in place, you can rest easy in the knowledge that your company has a hybrid working blueprint that will serve you well.
Have these tips helped you determine how you can create a safer and more secure device program for your hybrid workplace? Share your thoughts below!
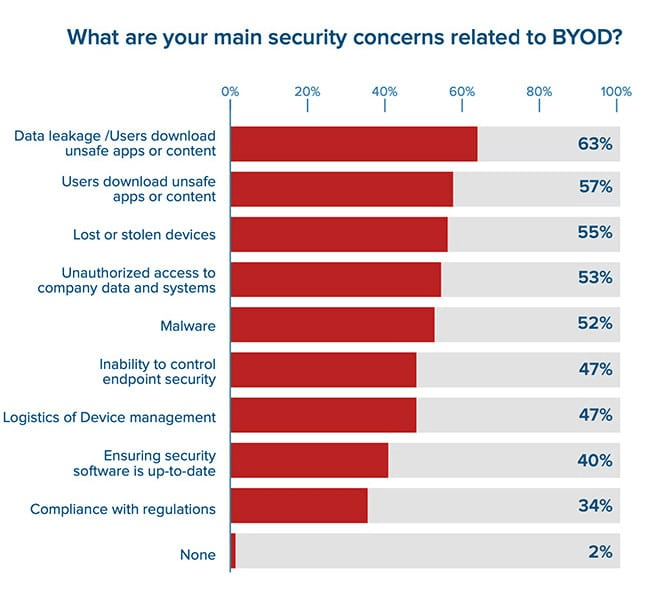
[…] an era where privacy is a growing concern of enterprises and consumers, this level of exposure could cause significant damage to a business […]