Last Updated on August 4, 2022
When mobile device management started to take off in the early noughties, not many people foresaw or predicted just how ubiquitous mobile devices would become later in the century. In the United States, there are actually more mobile phones in use than there are people. Around half of Americans now own some form of a tablet device and over half own a laptop or notebook.
The prevalence – continuing to grow – of these devices caused a trend known as BYOD, or Bring Your Own Device. This trend saw employees bringing their own devices to work for business purposes, and using them to access networks and systems in their workplace.
At first, the advantages seemed limitless, as employers no longer had to fork out to provide their staff with work devices. However, the rise of data as one of the chief phenomena of the 21st century quickly put a stop to that.
People started to realize that bringing a device into work was incredibly insecure. Employees could access confidential – and expensive – data, the security of which could not be vouched for outside of the workplace.
So mobile device management was born, less out of a desire to stop employees from playing Candy Crush and more to make sure they were accessing work networks securely.
Mobile device management solutions are essentially pieces of IT technology that allow a central system administration to manage all devices connected to a network remotely and to remotely control devices too. These systems mostly protect and oversee the transfer of data between different devices and types of devices on a network.
With the growth of remote working, especially in the time of a pandemic, questions about BYOD security, and the accessing of work networks from home, have now been raised again.
Most enterprises employing significant numbers of work-from-home employees will have to think about a mobile device management solution. Below, we talk about ten different must-have features for this, which are absolutely necessary and entirely non-negotiable.
A reminder, though: choosing a solution for mobile device management is just like looking for a new car or Talkdesk alternatives, in the sense that every product is tailored to a slightly different design. It’s up to you to decide what the priorities are for the solution you end up selecting.
1. A trial period
This might not be a feature necessarily, but it is essential. Whatever solution you end up choosing off the shelf should have a trial period. There are two reasons for this.
The first is to test the actual implementation of the mobile device management solution, to work through bugs or any other kind of technical problems, and make sure that everything goes smoothly. It’s important that if there are any major technical issues that you can’t solve, the provider has the maximum incentive to help you work through them.
The second is to trial the use of mobile device management on a select part of the workforce so they can spread positive commentary about its use and allay the fears of other workers. Even in the strongest of businesses, there can be suspicion or even hostility about allowing system administrators access to personal devices.
It’s important that staff know that MDM is for productivity and data safety, not so your manager can see your latest ‘video chat: what you need’ Google search.
Good words from trusted and honest colleagues can help defuse any of those understandable feelings. Over time you might find that staff satisfaction has actually risen due to an efficient and useful MDM.
If you find the rolling out of your mobile device management solution hasn’t gone according to plan, then a trial period means you aren’t locked into paying for something that doesn’t work. MDM helps to keep your data and system secure, so it’s worth taking your time and implementing it carefully.
2. Location tracking
As an actual feature, location tracking is an obvious one. Your employees naturally have the right to take their devices wherever they want to, but even the most conscientious worker can sometimes forget to sign out of a network. In the case of a lost – or worse, stolen – device, location tracking can help recover it.
While you can sell this to employees as being helpful rather than intrusive, the fact is that if they’re not logged onto the network, the location tracking won’t help them and won’t give you any information. It only comes into force if they lose a device that a third party could use to gain access to sensitive data.
3. Remote wiping
Another feature related to location tracking is remote wiping. In an emergency, when a device is lost and can’t be recovered, or its location can’t be determined, the system administrators can remotely wipe sensitive data from the device.
This is, of course, a last ditch security option, but it’s a necessary one nonetheless. It’s another layer of security for your data, and you do need the ability to wipe data from a remote device.
4. Troubleshooting
Devices have problems all the time, whether these are actual software or hardware problems or due to unaccustomed or inexperienced users. In a traditional IT support setup, an office has an IT team who can address problems in person, but this is not helpful when working remotely.
Even phone-based troubleshooting can be problematic, as trying to describe an IT problem over the phone is beyond the ability of some. If an employee needs help using some free business programs then your IT department needs to be able to assist them remotely.
Good MDM solutions tend to build troubleshooting in. Of course, they won’t be able to come round and fix faulty hardware, but a central administration can determine problems, and solutions, remotely – especially useful for staff working from home. So make sure your MDM solution has a good troubleshooting package.

5. Over-the-air distribution
Simply put, over-the-air distribution is a method of delivering updates to software wirelessly. Of course, this counts for any kind of software, from apps like Flock to Skype and so on.
However, there are all kinds of things you need to push over the air that you might not have thought about: software and firmware updates for one, but also, and especially important for security, antiviral and other data protection measures.
Especially as data protection regulations are updated, the ability to enforce the strictest data protection policies across all devices by over-the-air distribution is useful, so consider carefully the OTA systems in any MDM solution you choose.
6. Device Security Management
Security management is one of the most important parts of any mobile device management solution, and the reason for the large recent uptake in mobile device management. Proper security management allows you to effectively protect the data you store, which is both valuable and expensive, and a source of privacy invasion concerns.
Proper security prevents leakages of data. It’s not that employees can’t be trusted, but that compliance with data protection and security policies is often difficult to train and difficult to enforce.
Good device security management lets you rest at ease, so you should pay particular attention to this when selecting an MDM solution.
7. Device inventory management
Device inventory management is probably one of the simplest features your mobile device management solution needs, although that doesn’t mean it should be overlooked.
Simply speaking, inventory management catalogs all the different types of devices connected to your network, who owns and uses each one, what operating systems they use, and so on. It allows you to ‘zoom out’ and examine broadly the kind of BYOD policy you can design, since you know the nature of the devices your employees are using.
This is especially useful in a remote world where it is harder to gather in-person information.
8. Device Content Management
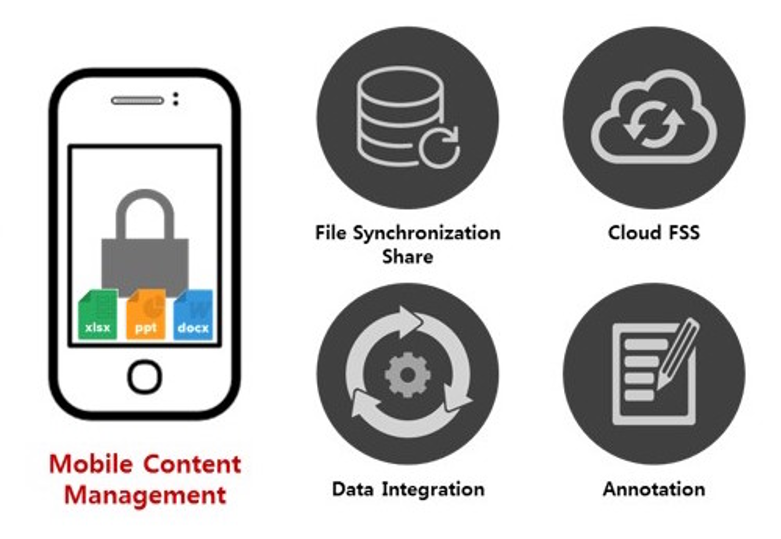
Content management is one of the most useful additions to a mobile device management system. It creates portals that allow you to remotely distribute files and content to the entire network from a central administration, transferring content to employees without having to email it out and ensure it has been downloaded.
In this sense, device content management can also be considered a productivity tool.
It is sometimes known as mobile content management (MCM) and sold separately to mobile device management. We’ve included it here, however, because it can be a core component of an MDM system.
A mobile device management solution can sometimes come with its own proprietary content viewer for those on the network to examine files sent via the MCM. It can also be used as a form of joint file storage that is accessible across a whole network.
The type of files that an MCM can deal with varies, so that is something you need to question and examine when selecting a mobile device management solution. Virtually all MCMs should be able to transfer and open .mp3 extensions, for instance, but some may not allow the use of .flac file extensions. There are other examples, but the main thing is to be absolutely sure of the capabilities of the solution you choose.
9. Service support management
The specific features of a mobile device management system are extremely important. However, one logistical matter that we might sometimes ignore is crucial too – what is the level of customer service offered by the provider?
Software-as-a-service providers necessarily have to offer good service support, but exactly what you are looking for depends on the needs of your business. The more flexible the provider is on giving service support that is useful, the better for you.
For example, if your IT team is relatively small, rolling out the actual solution might be the hardest part. If your business is sprawling, with many different devices, then maintaining the system is more difficult than if you are just applying BYOD to Windows notebooks. And if you already have a mobile device management solution in place and want a new one, what kind of conversion support can you expect?
Some of these support features are offered automatically, but others may need negotiating, depending on your business and what it does.
10. Levels of reporting
Last but not least, one feature of your mobile device management solution that should be carefully examined is the levels of reporting – in other words, what information can management glean from those using the network and the associated MDM?
Questions might include:
- How flexible are the reporting systems?
- Can the MDM generate reports and at what levels?
- Can the MDM generate reports that provide answers to regulators or any person involved in auditing compliance?
One of the most useful features of an MDM is its ability to reliably and flexibly demonstrate compliance with regulations or policies to those tasked with auditing that information. In this regard, not only does the MDM offer security, showing where compliance might be lacking, but it also saves time and effort typically expended on project management.
This is especially important for sectors or industries heavily dependent on compliance, especially data compliance, like healthcare and finance, but the ability to report on the overall use of the system and network can give interesting information to managers at all levels.
You want to look for flexibility, reliability, and detail here. A high level of automation in reporting is also useful from a business efficiency perspective.
Every mobile data management solution has its own utility and the one you select depends on your exact needs, so it’s important to shop around and look for an option that compliments you and your digital workforce.
Consider some of the above features – which are most important to you? Which will add more value to your business and help secure it better?
The features we have listed are not exclusive. Others, like team messaging, can be found on some mobile device management solutions too.
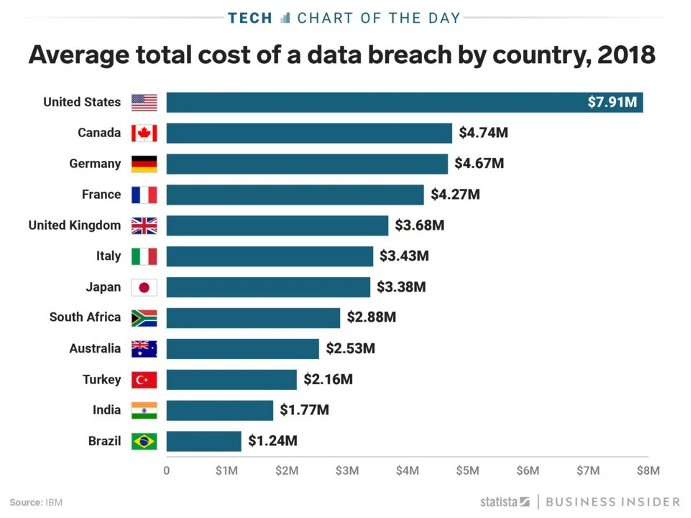
Either way, regardless of the cost of a good mobile data management system, you should take it very seriously. That’s because, according to Capita, the average data breach costs $3.86 million and takes 280 days to identify and contain. Other sources put that number much higher.
As with many things in life, prevention is better than cure, and mobile device management should be an important part of your prevention scheme.
Author Bio:
Elea Andrea Almazora – RingCentral US
Elea is the SEO Content Optimization manager for RingCentral, the leader in global enterprise communication and collaboration solutions on the cloud. She has more than a decade’s worth of experience in on-page optimization, editorial production, and digital publishing. She spends her free time learning new things.
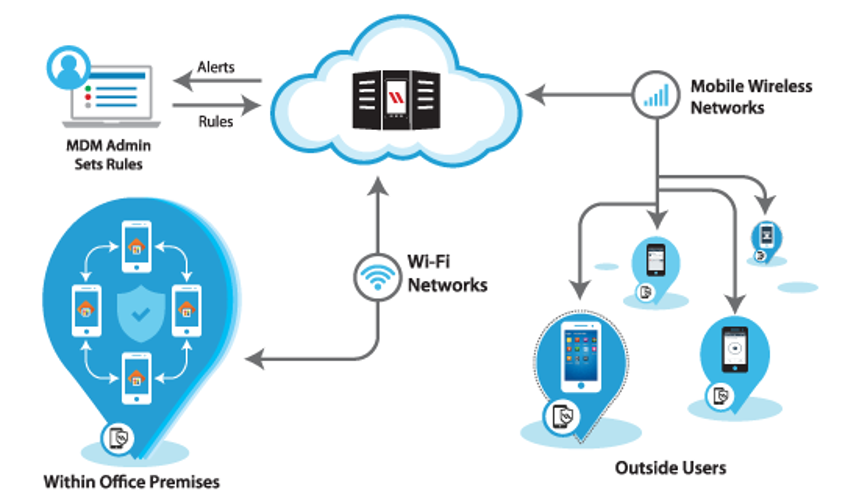
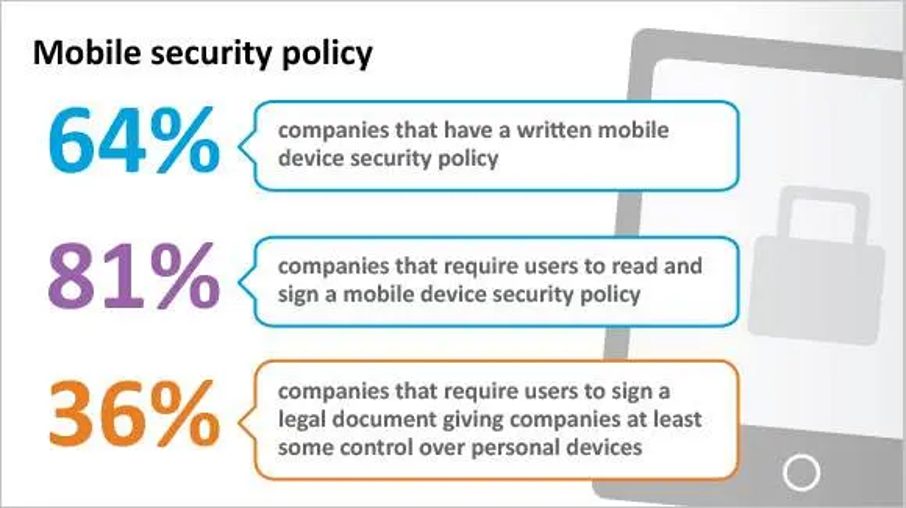

[…] and security of mobile devices within the company while protecting the company network. The main features of MDM software […]
[…] tests: They confirm whether key features of an application are working correctly. The application must pass this test before it’s […]
This has to be one of the better articles I’ve seen on MDM, I like the fact that you’ve included data breach figures. Certainly the Cyber Essentials scheme in the UK now requires either mobile security or application whitelisting (such as Android Enterprise via MDM) which is a great step.