Last Updated on September 1, 2022

It’s no secret that information security is widely considered unexciting; when IT professionals start talking about the subject, most people feel their eyes glaze over and their minds wandering elsewhere. But, regardless of the thrill factor, it’s still worth being familiar with information security and some of the different types available.
The most relevant form of encryption to the AirDroid Business platform is Transport Layer Security (TLS). In essence, TLS encryption protects data sent over the internet to ensure that eavesdroppers, hackers, or anyone with malicious intent are unable to see the data being transmitted, and this is particularly useful for private or sensitive information, like passwords, financial or payment information, personal correspondence, or confidential business information.
What exactly is TLS?
TLS is a cryptographic protocol that provides end to end security for data sent between applications over the internet. It’s mainly found on secure web browsers, its presence signaled by the padlock icon that appears in the browser bar when a secure session is established.

Its applications extend further than just browsing, however, with uses across a number of applications – including email, file transfers, video and audio conference calls, instant messaging, VOIPs, internet services like DNS and NTP, and of course, on some MDM platforms like AirDroid Business.
The function of TLS encryption within the AirDroid Business platform mainly relates to the transfer of information – with the encryption protecting files when the two-way file transfer function is in use. This encryption also extends to the application management services, or AMS suite, where data contained in forced installations and update rollouts are also protected by TLS encryption.
TLS was born out of its predecessor, Secure Sockets Layer, or SSL encryption. This method of encryption was developed for use in the 90s on traditional Netscape browsers. However, TLS was designed to give the security that SSL couldn’t outside of Netscape: thus, it’s usable across all networks and data streams – and it works! – which is why TLS became the industry standard. It’s also why AirDroid Business uses TLS encryption within its two-way bulk file transfer function.
It is worth noting the limitations of TLS encryption, however, is that it only works for information or data in transit. Data and information stored on devices are not protected by TLS encryption, so additional security measures should always be taken by businesses looking to protect stored data and online accounts. Some of these measures include:
- Backing Up Data Regularly
To put it simply, backing up data refers to making copies of files contained within a device, and if it’s not a part of a businesses’ IT management plan already, it should be. The basic rules of backing up data are simple: keep at least three copies of your data backed up at all times, store the data in at least two different formats (hard drives, cloud storage, etc.), and keep one copy off-site to protect against flood, fire, and theft.
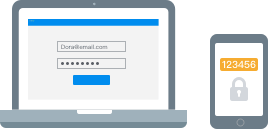
- Using a Two-Step Verification on User Log-ins
Two-factor authentication is an important measure to take in making your data more secure online, and it works by requiring users to follow two different steps in proving their identity. This form of security will generally be used within phone banking apps. It’s also an available feature on AirDroid Business, where administrators can enable two-step verification via the admin console.
- Role-Based Access Control
Role-based Access Control, also called RABC, is a feature of AirDroid Business, allowing the administrators to control permissions in relation to which files certain users can access. This is especially important in companies with different management tiers, where certain functions and files should be accessed by certain people. Within the AirDroid Business Solution, there are three tiers of access: administrators, who can manage and control all devices, Team Members, who can assist in managing devices, and Viewers, who are able to access specific devices within a specified timeframe.

[…] Encryption […]