Last Updated on February 3, 2023
Cybercriminals are a threat to businesses, but research has shown that data breaches caused by employees happen a lot more frequently than we anticipated, whether it is intentional or accidental. In fact, according to IT Governance, “of all the data breaches caused by employee error, accident and negligence were the most common cause, accounting for 51% in 2021, followed by malicious insiders.”
Therefore, businesses should take proper measures to protect their IT assets and sensitive information from both. This is where User Management Systems play an important role for businesses—to protect company data and ensure all users have the appropriate access privileges to internal systems and resources.
What is User Management?
User Management, also called UM, describes the ability for administrators to grant access, monitor, and control user activities within an organization. It is often paired with cloud-based identity and access management (IAM) and role-based access control (RABC) to empower administrators with much greater control over their digital assets.
More precisely, it allows organizations to control and audit who comes in and out of their organization’s network and resources, as well as to define which resources an employee or end-user will have access to and which will be restricted based on their individual role.
In addition, these management systems make it possible for administrators to track user activities more effectively. For example, when a company works with outsourced contractors or specialists, by implementing a user management system in its IT infrastructures, will allow them to control how much and to what extent its resources can be accessed by external users, and also prevent any unauthorized access.
An efficient user management solution should include the following features:
✓ Create, manage, and remove user accounts.
✓ User identification (user name, password, authorization/IAM systems, etc.)
✓ Assign user access privileges for systems, services, and/or applications
✓ Protection against unauthorized access
✓ Data tracking on user activities
Why is User Management Important?
User Management makes it easier for IT administrators to manage their company resources and users’ accessibility, maintaining the security of digital assets and sensitive data. Having the ability to set different permission levels for certain users can drastically strengthen both the security and the operations of an organization.
The implementation of user management can help eliminate friction and frustrations caused by system unfamiliarity or complexity and therefore, leading to a better end user experience. There are also parameters and automation that can be set to detect and notify suspicious activity, communications, or events, enabling organizations to minimize the likelihood and impact of data breaches more effectively. All of these are vital to building a secure digital environment for businesses today.
With the growing demand of cloud services today, user management has become a crucial component that is being used in a wide range of user-based platforms. For example, for Managed Service Providers (MSPs) and Project-Based Businesses, user management is crucially important as it enables them to create and assign separate sets of access permissions for their clients so they can take a quick checkup on their IT assets when needed without messing around with the system settings or accidentally breaching other company’s data privacy.
Managing users in AirDroid Business
AirDroid Business offers a seamless process of inviting and managing users in your organization, making sure all users in the system are present and authorized. It includes both IAM and RABC mechanisms for IT admins and business owners to assign roles and access privileges to their team members or end-users based on their roles and job functions. This is especially important in companies with different management tiers, where certain functions and files should be accessed by certain people only. This is a feature that can ensure businesses maintain a clean user base and a safe IT infrastructure across the organization.
Here we will take a deeper look at each function offered in the user management system in our mobile device management solution.
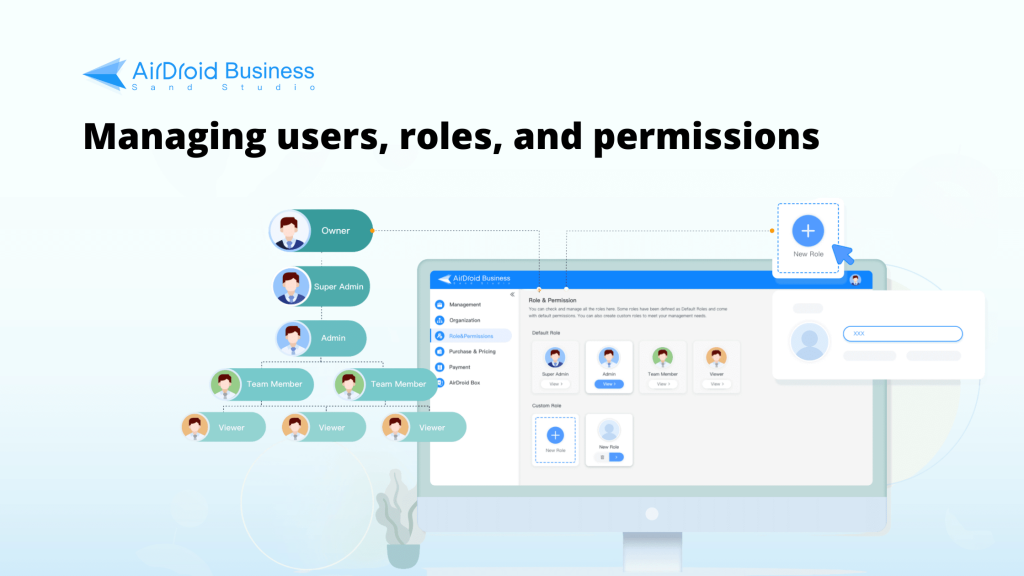
Roles and Permissions
A role is a set of permissions that you can assign to any users you invited into the system and that determines what this user has access to, usually depending on their job functions.
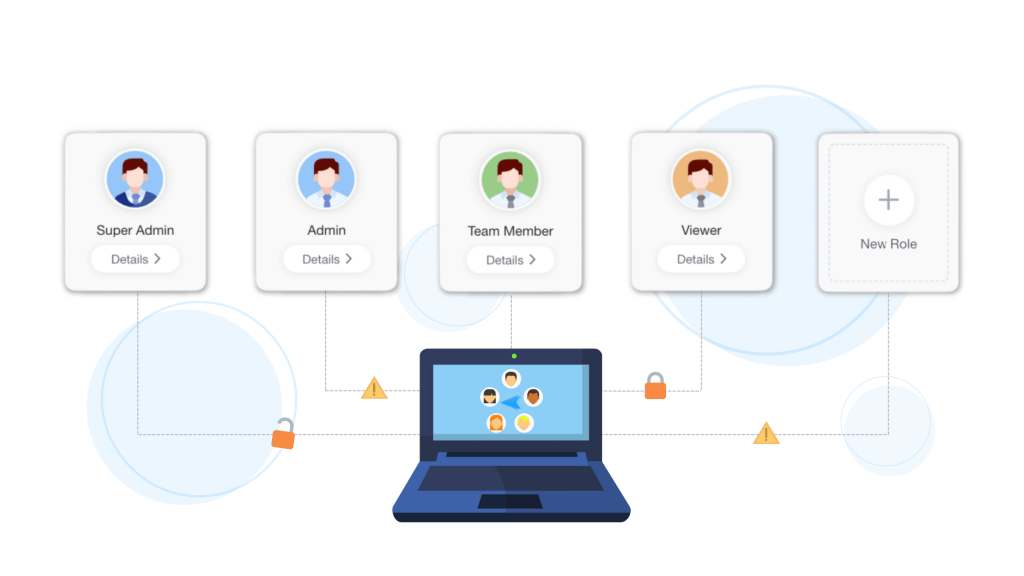
There are five types of default roles in AirDroid Business that you can quickly apply to your users in the Admin Console. Each comes with a set of different permission levels that determines what users with that role can access and do in the console (from highest to lowest): Owner, Super Admin, Admin, Team Member, and Viewer. AirDroid Business MDM also supports customizations of roles and permissions that can be tailored to the needs of your organization.
a) Default Roles
Default Roles are a quick way to assign roles with a preset of access privileges and permissions to your users when inviting them to the MDM console. In AirDroid Business, there is a total of five default roles.
- Owner is the user who signed up for the AirDroid Business account. The owner has access to all features and system settings, including making payments for the subscriptions.
- Super Admins act almost the same as the account owner but without permission to make or change the payment options. This role can access all features and data and can configure all system settings and user permissions.
- Admins are able to use and access most of the functions and data but with a couple of limitations: no permissions to Device Map and Geofence settings.
- Team Members have access permissions to Remote Control and Device Monitoring features with a few limitations to functions and settings in the Device Dashboards and Workbench.
- Viewers can only monitor devices remotely and are not allowed to access any other functions or settings in the Admin Console.
Please note that there can only be one owner per AirDroid Business account, whereas you can have as many Super Admins, Admins, Team Member, or Viewers as you wish. See the table below for a complete list of all the permissions that are given to each role:
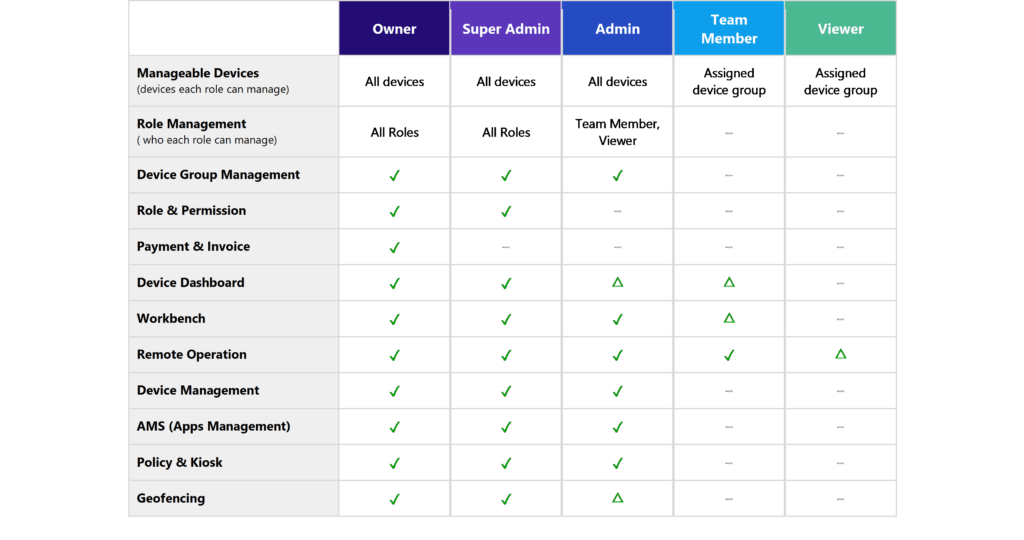
🚩 View the complete table of roles and permissions comparison lists.
b) Custom Roles
You can assign certain permissions to users by creating custom roles based on the specific needs of your organization. When creating custom roles, you will need to understand the roles that your organization supports and the scope of their project to know exactly which accessibility and permissions are needed for their work. Admins are able to choose whether the user 1) has access, 2) has no access permission, or 3) can only view the data of each available function in the system.
In AirDroid Business, you can create as many roles as needed to ensure only the users of your choice can access certain functions, modify the system or device settings, create device groups, etc. For example, if you wish to let your clients view the status of their remote devices, you can then create a new role called “Client Company A” with only the permission to view their own devices’ status from the Device Dashboard. You are also able to update a role’s permissions or alter a user’s role at any time; the changes take effect immediately.
🚩 Learn step-by-step on How to create custom roles and permissions in AirDroid Business.
Account Activity Reports
AirDroid Business also offers reporting features for business owners and IT managers to get a more granular view of its company devices and its users’ activity within the system. One of our reports in the Workbench—Account Activity Report—allows admins to monitor all types of activities that have been done on the account, including account actions, device enrollment history, changes to settings, updates on apps, and more. Reports like this are very practical for organizations with several admins controlling different groups of devices. Administrators are able to track the historical activities on devices, and most importantly, they can monitor how the devices are being used by their account users.
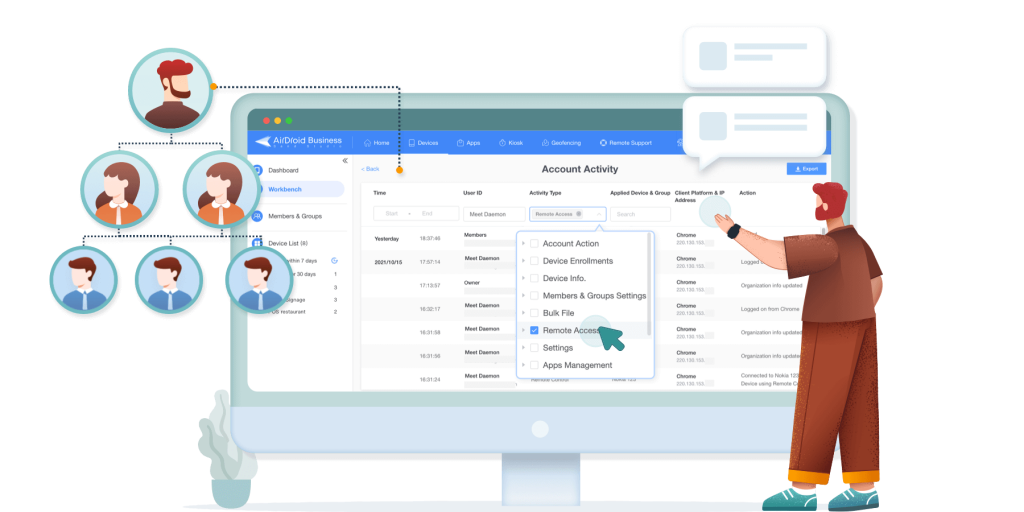
Take one of our customers’ use cases as an example: they wanted to find out the reason for an unusual data surge coming from one of their remote devices, so they would go to the Account Activity Report to track down the time when the device is using the most data and who was in charge of the device at the time. By identifying abnormal activities and finding out who was responsible for them, organizations can resolve issues quickly and prevent further loss more effectively.
🚩 Explore more about other Reports in AirDroid Business MDM.
Conclusion
Any organization should implement systems to protect its information and resources from being misused by its employees or users. User management systems ensure data is only accessible by selected users. This helps to enhance the security of an organization, minimizing the risks of data breaches or unauthorized access.
If you are looking for a Mobile Device Management (MDM) solution that comes with users and access management to simplify the tasks for managing users in your organization, AirDroid Business has all the features you need while offering top-notch device management and remote control features to streamline your business IT operations.
Sign up for a free account to start managing your Android devices today! You can also contact our sales representatives for more information on our MDM solution.

[…] the necessary authorizations before using the network. IAM software allows the user to simplify the user management process, such as password management or software dedicated to accounting management. For IAM […]